We’ve identified a campaign that advises people to vote for a contest so they can win “prizes”. The only “prize” is that they’ll lose access to their WhatsApp account. Multiple hints indicate that the campaign originates from Russia. This article written in Romanian presents general details about this method.
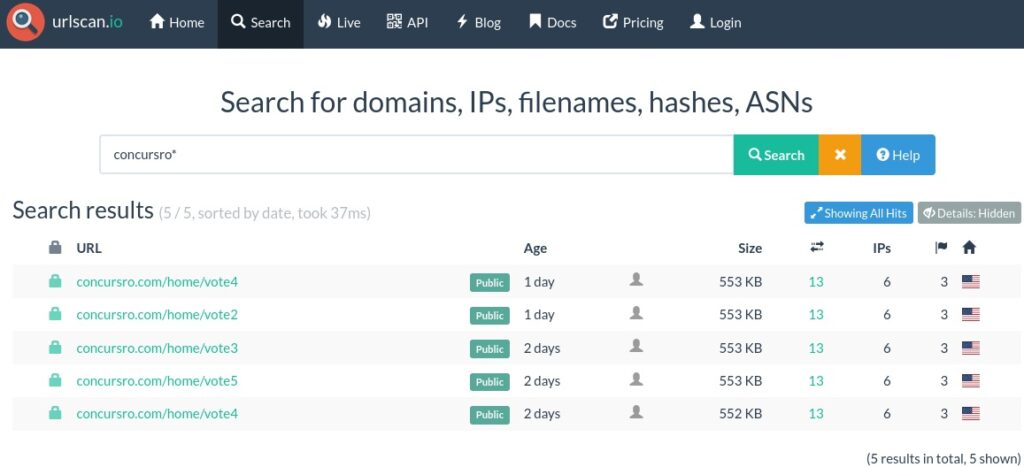
Users receive a WhatsApp message from friends or family that were previously compromised in the campaign. The message is in Romanian and encourages the recipient to vote in a contest. An example of the suspicious URL is https[:]//concursro[.]com/home/vote4:

We’ve used Urlscan.io to identify other domains from the same campaign. As we can see in Figure 2, multiple URLs were sent:
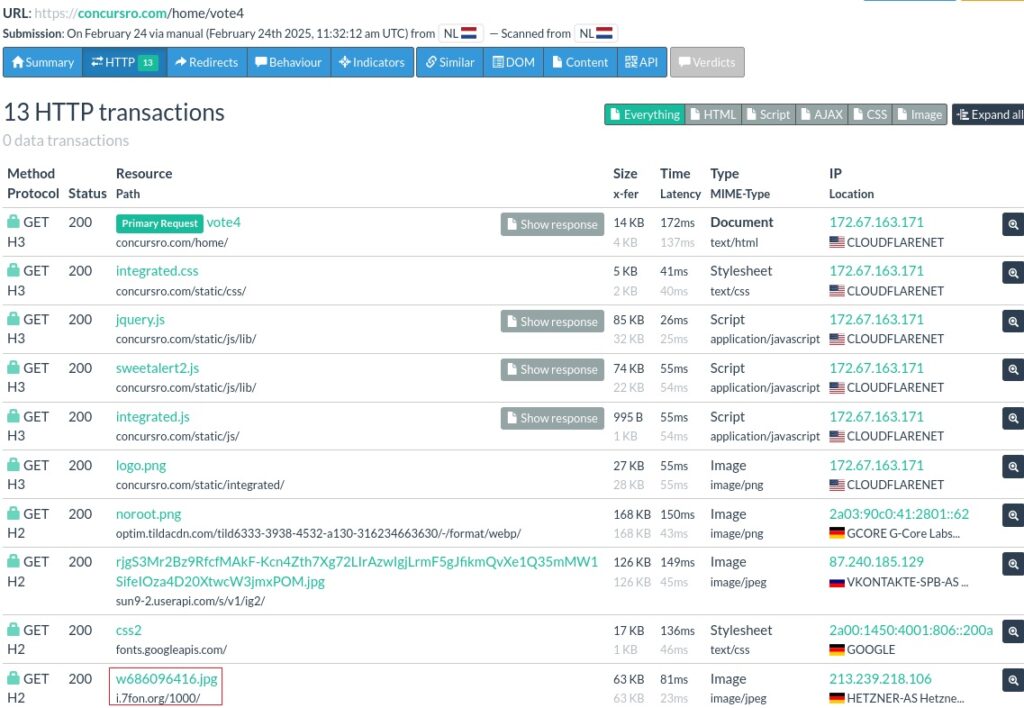
We’ve observed a GET request for an image called “w686096416.jpg” and another one for an image from the Russian social network VKontakte:
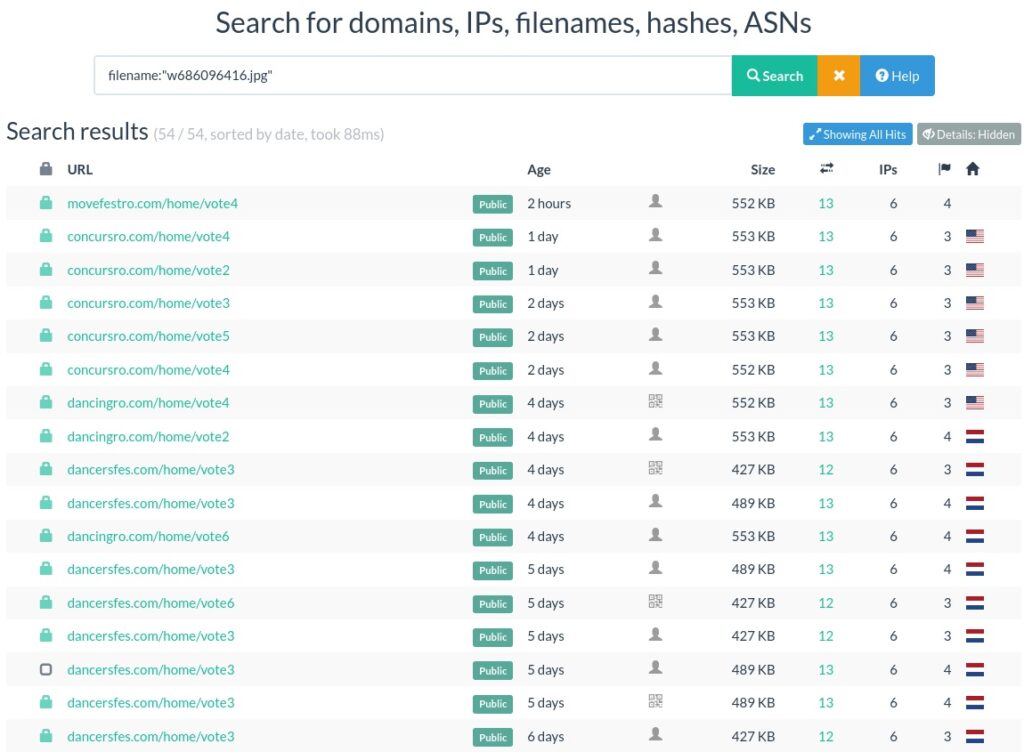
We can pivot on the image name and identify other URLs/domains that requested the same image, as displayed below:
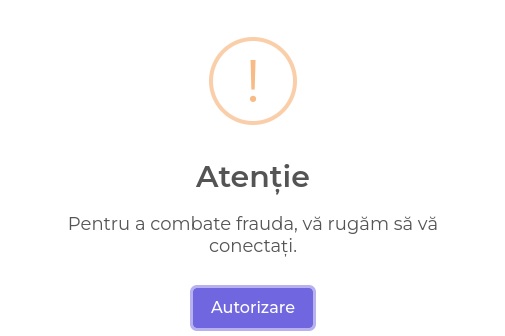
When an unsuspecting user clicks on the “Vote” button, the following message, which tells the user to connect in order to “combat fraud”, is displayed:
The user should input the WhatsApp number in the box. As we can see below, Russia is written with Cyrillic letters.
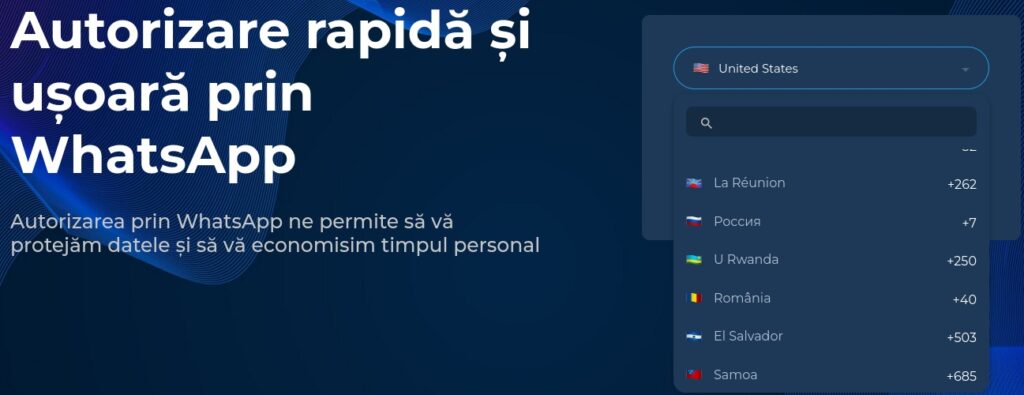
In this article it is presented the method to link a device with a phone number. The victim needs to enter an 8-character code, which is provided on the suspicious page (see Figure 7). At this stage, the attacker has access to the victim’s WhatsApp account.

The lang attribute that specifies the language of the content is set to “ru” (Russian language) on the first page:
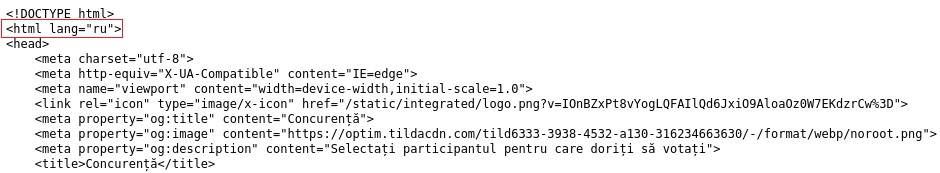
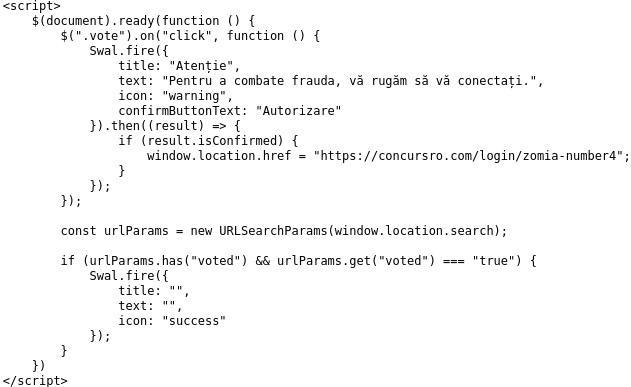
The script responsible for handling the “authorization” can be found on the same domain at “/login/zomia-number4”:
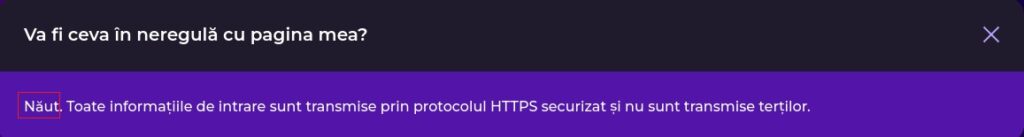
Some sections on the suspicious page contain Broken Romanian that should raise suspicion:
We’ve identified the following domains part of this campaign:
concursro[.]com
dancingro[.]com
dancersfes[.]com
rocondance[.]com
rodancee[.]com
rofesting[.]com
danccingro[.]com
rodaciing[.]com
dancerofest[.]com
danciingro[.]com
rodancehit[.]com
rodancing[.]com
rodence[.]com
dancechoise[.]com
festdance[.]com
coonnkurenta[.]top
concursdedans[.]com
concursiarna[.]com
dancersro[.]com
dancingvot[.]top
showdance[.]top
votingdance[.]top
dancevotr[.]top
dancefesting[.]top
feastdance[.]top
danceiivot[.]top
Based on pivoting on another resource, we could determine that the attacker targeted English and Turkish speaking users in the past:
- https[:]//starsdance[.]top/home/vote32 – English page
- https[:]//starsdance[.]top/home/vote101 – Turkish page
The threat actor has access to the victim’s WhatsApp account after entering the 8-character code and continues to send the same voting message to his/her contacts. As a consequence, the victim might lose the WhatsApp account because of spamming, as reported by multiple people on Reddit.
We advise users to not enter 8-character codes from dubious websites to access their WhatsApp account. We will continue monitoring the campaign and update the blog post if necessary.
Great research